Preconditions
- An active ADFS server is installed. for instructions on installing an ADFS server, please see the Appendix at the end of this section
- Totara/Moodle needs to be SSL enabled. If not, an SSL certificate is needed.
- Note that clients are able to either provide Kineo with an SSL certificate or one can be purchased on your behalf by Kineo.
Step 1:
Kineo need your federation XML configuration file.
The file can be obtained at https://adfs.com.au/FederationMetadata/2007-06/FederationMetadata.xml adfs.com.au being the domain of your ADFS server.
The configuration file contains the following details allowing us to configure our endpoint inTotara/Moodle
- SSO end point URL for sign in page
- Single sign out URL if there is
- Certificate for authenticating SAML responses
Step 2:
After we receive your federation XML, we will give you our SAML metadata for creating a relying party.
To create a relying party follow the steps below:
- Open the AD FS 2.0 Management Tool, open "Trust Relationships", right click on "Relying Party Trusts" and click "Add Relying Party Trust":
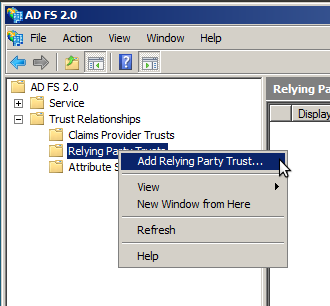
- Click start and on the next screen choose to import form a file and pick the file received from us. Click next and dismiss the warning
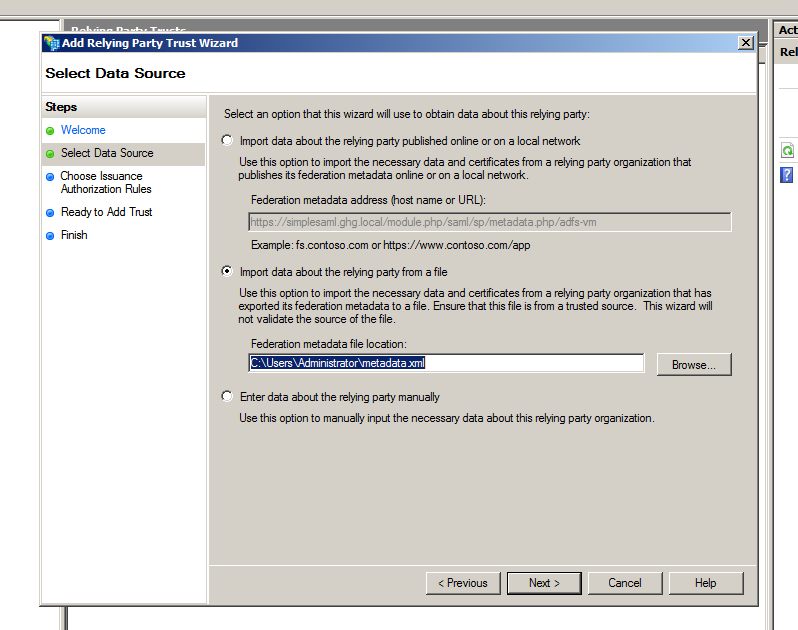
- Choose "Permit all user to access this relying party" and click next (you can choose a particular group depending on your organisation)
- Click close to finish the Wizard
- On the AD FS window, click "Relying Party Trust" and click Edit Claim Rules
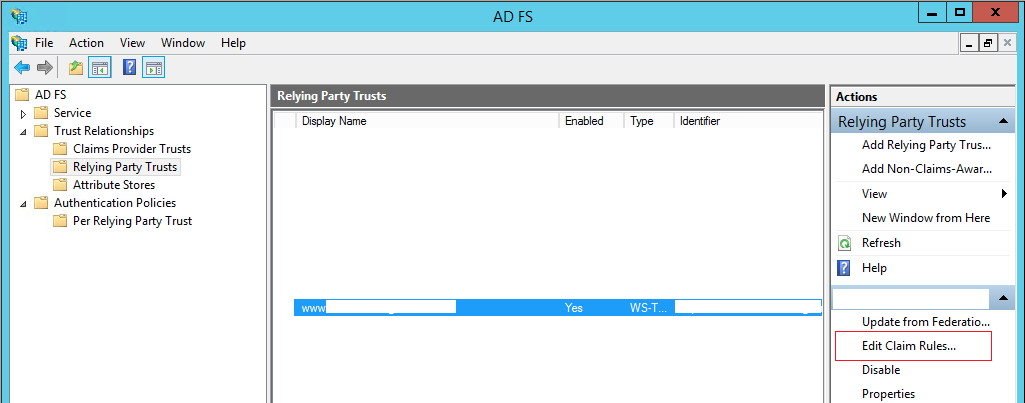
- On the dialog box "Edit claim rule for…", on tab Issuance Transform Rules, click "Add rule"
- Select Send LDAP Attributes as Claims and click next
- Give the rule an appropriate name.
- Select Active Directory for the Attribute store
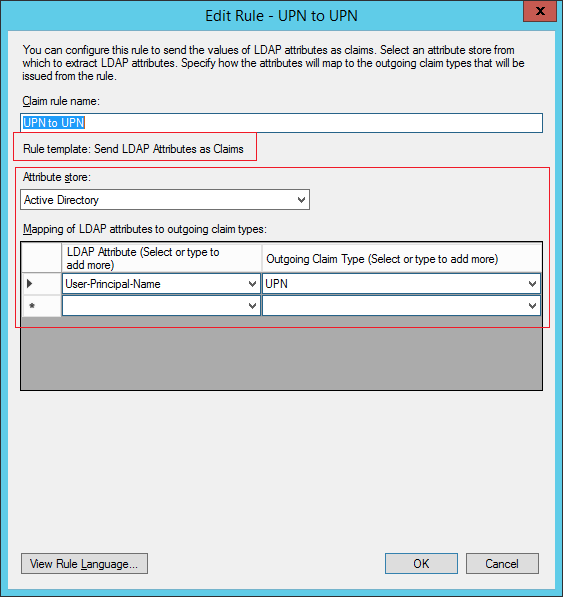
- Add the following mapping: User-Principal-Name => Name ID
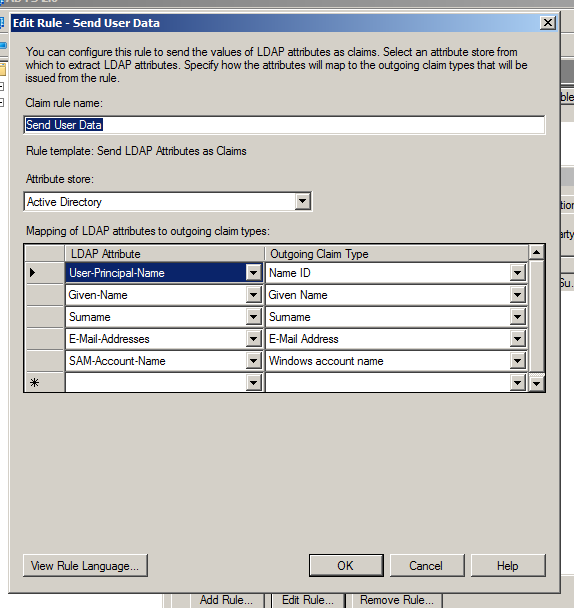
Note: It is possible to map other attributes, but this isn't important if the intention is to use HR Import for importing users and SAML is intended to be used only for SSO.
Additional Rules
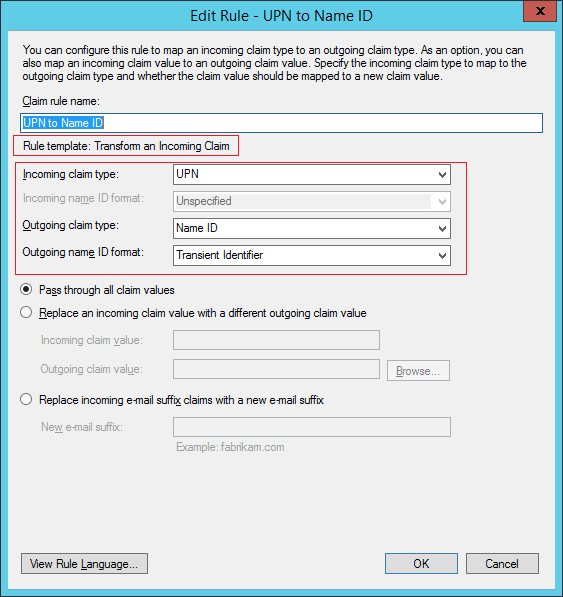
In some systems with UPN, we need to add 2 rules: map LDAP to UPN, then UPN to Name ID for it to pass the username properly
Rule 1: User-Principal-Name to UPN
Rule 2: UPN to Name ID
In the "Issuance Authorisation Rules" tab, configure Permit Access to All Users (depending on your specific needs)
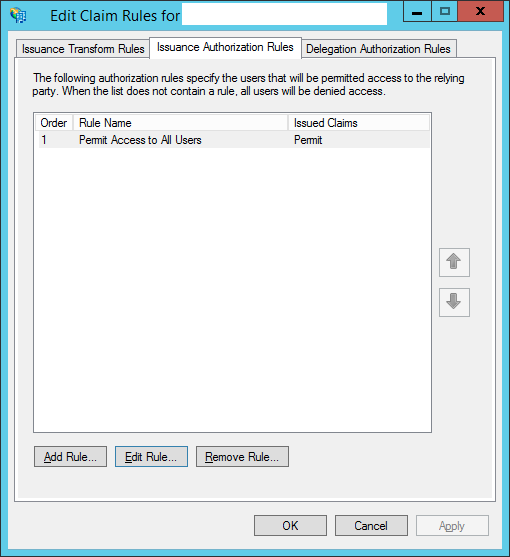
Click OK to close the dialog box.
We then need to create a test user:
- Navigate to 'Active Directory Users and Computers'
- Expand 'forest.local'
- right click on Users
- select New -> User
Step 3:
Return details of the test user to Kineo
Appendix: Setting up an ADFS server
To install ADFS server, follows the step below
- Download and install Windows Server 2008 (Enterprise Full)
- Check that the time zone and date/time are correct.
- Change the computer name to something easy to remember, like WIN-SAML (that's how we will be referring to it from now on).
- Download and install all updates including Service Pack 2
- Using Add Roles add the Active Directory Domain Services.
- Run dcpromo.exe from the command line.
- Select the option to Create a new domain in a new forest.
- Give a name to your Forest Root Domain (FQDN), e.g. forest.local.
- Set the functional level of the forest to Windows Server 2008.
- Make sure DNS Server is checked under Additional Domain Controller Options. Continue using a dynamically assigned IP address. If any errors appear for delegation etc, just continue.
- Reboot on completion.
- Using Add Roles add the Active Directory Certificate Services.
- Select only Certification Authority.
- As a Setup type select Enterprise.
- As CA Type select Root CA.
- Create a new private key using the default options.
- Using Add Roles install Web Server IIS. Add any required features as prompted. Use default settings.
- Open Server Manager.
- Go to Roles > Web Server (IIS) > Internet Information Services (IIS) Manager.
- On the window that appears on the right, go to WIN-SAML (FOREST) > Sites > Default Web Site.
- On the actions tab on the right, click Bindings under Edit Site. Bind https and select as an SSL certificate WIN-SAML.forest.local.
- Then, double click on the SSL Settings icon, select Require SSL and click Apply on the right.
- Download and run Active Directory Federation Services from http://www.microsoft.com/download/en/details.aspx?id=10909. If you are having any trouble downloading using Internet Explorer, download and install Mozilla Firefox and try from there.
- Make sure you select Federation server as a Server Role.
- When the wizard is finished, select the Start the AD FS 2.0 Management snap-in when this wizard closes checkbox and click Finish.
- When the management tool opens click the link to start the Federation Server Configuration Wizard.
- Choose the option to create a new federation service.
- Choose to create a stand-alone federation server.
- If there are multiple SSL certificates on the machine you will have to choose one but in most cases you can accept the default.
Comments
Related articles